There are many reasons you might want to reset a password:
- Someone gave you a computer with Ubuntu installed on it but not the password for the user account.
- You just installed Ubuntu and forgot what password you selected during the installation process.
- You have too many passwords in your life and can't keep track of them all.
- Or you might want to hack in your Friends System.
Well, this tutorial will help you reset your
Ubuntu user account password, regardless of what reason you have for
resetting it.
First, you have to reboot into recovery mode.
If you have a single-boot (Ubuntu is the only operating system on
your computer), to get the boot menu to show, you have to hold down the Shift key during bootup.
If you have a dual-boot (Ubuntu is installed next to Windows, another
Linux operating system, or Mac OS X; and you choose at boot time which
operating system to boot into), the boot menu should appear without the
need to hold down the Shift key.
From the boot menu, select recovery mode, which is usually the
second boot option.
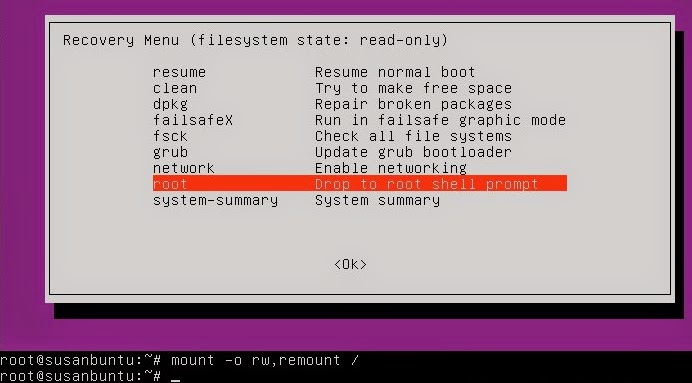
After you select recovery mode and wait for all the boot-up processes
to finish, you'll be presented with a few options. In this case, you
want the Drop to root shell prompt option so press the Down
arrow to get to that option, and then press Enter to select it.
The
root account is the ultimate administrator and
can do anything to the Ubuntu installation (including erase it), so
please be careful with what commands you enter in the root terminal.
In recent versions of Ubuntu, the filesystem is mounted as read-only, so
you need to enter the follow command to get it to remount as
read-write, which will allow you to make changes:
#mount -o rw,remount /
If you have forgotten your
username as well, type
#ls /home
That's a lowercase L, by the
way, not a capital i, in ls. You should then see a list
of the users on your Ubuntu installation. In this case, I'm going to
reset Susan Brownmiller's password.
To reset the password, type
#passwd username
where username is the username you want
to reset. In this case, I want to reset Susan's password, so I type
#passwd susan
You'll then be prompted for a new password. When you type the
password you will get no visual response
acknowledging your typing. Your password is still being accepted.
Just type the password and hit Enter when you're done. You'll
be prompted to retype the password. Do so and hit Enter again.
Now the password should be reset. Type
#exit
to return to the recovery menu.
After you get back to the recovery menu, select resume normal
boot, and use Ubuntu as you normally would—only this
time, you actually know the password!
Note:
Some people get freaked out about having recovery mode logging you in as root. For more information, read Recovery mode makes me root user. Isn't that a security risk?
Some people get freaked out about having recovery mode logging you in as root. For more information, read Recovery mode makes me root user. Isn't that a security risk?